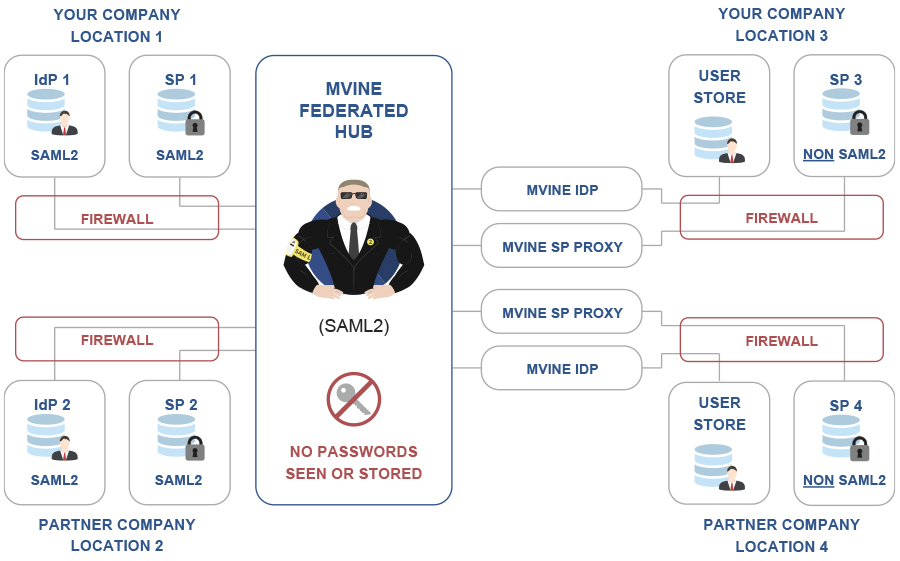
Identity and Access Management
So long as your users stay behind the firewall, you can design security policies that protect access to your business applications. What happens when access is required to cloud based applications. In this case cloud SSO providers require you to create yet another directory or virtual identity source. Even more a problem, what do you do when you need to give clients and/or partners access to your applications, whether they be without or outside of your firewall! Another bigger identity store with users from outside the organisation!